Cold has uncovered new clues regarding the likely contents of an encrypted hard drive seized from the West Valley City, Utah home of Josh and Susan Powell on Dec. 8, 2009, one day after Susan disappeared.
The Josh Powell hard drive was encrypted and has never been accessed, in spite of extensive efforts by law enforcement and ongoing work involving private digital forensics experts.

It is not clear whether or not the device might hold clues pointing to Susan’s whereabouts. However, breaking the encryption could reveal new information about Josh’s activities in the weeks prior to the disappearance.
The Josh Powell Hard Drive
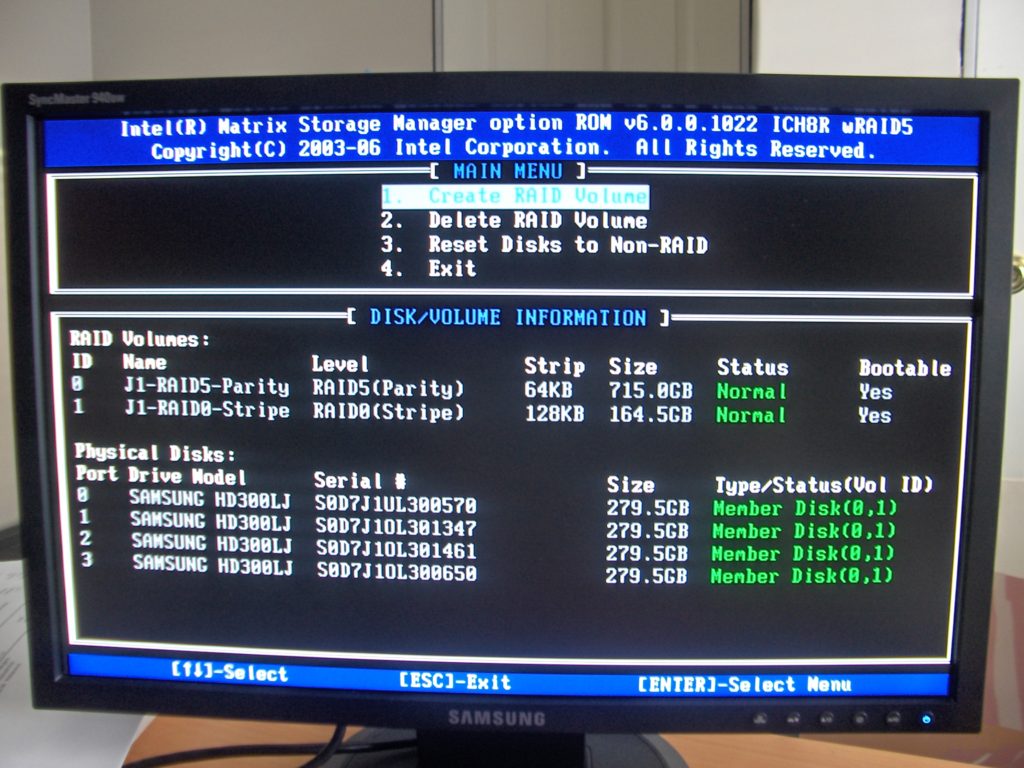
Detectives seized the device in question while serving their first search warrant at the Powell family’s home on Sarah Circle in West Valley. They located it in the downstairs bedroom that Josh used as his home office. The Western Digital-brand MyBook World Edition was connected by way of an ethernet cable to Josh’s home network.
The MyBook World drive had been in that same position for at least a year and a half. Susan pointed it out while recording a video documenting the family’s assets in July of 2008.
“This is some type of backup device,” Susan said in the video. “It says WD on the side. I don’t know, it like shares the information somehow.”
West Valley police investigating Susan’s disappearance discovered the MyBook World drive was inaccessible after delivering it to the FBI’s Intermountain West Regional Computer Forensic Laboratory or RCFL in Salt Lake City. Based on the FBI’s analysis, it appeared the whole drive had been encrypted using a freeware tool known as True Crypt.
ViceVersa Pro
Not all of Josh Powell’s hard drives were similarly encrypted. While reviewing data from Josh’s other computers and digital storage devices, investigators flagged several files referencing encryption, hoping to discover possible passwords or other insights that might help them gain access to the MyBook World drive.
One of those files resided on an array of hard drives in Josh’s desktop computer tower. It had the file name vvdb1NetworkEncrypted.tdb.
The Cold podcast obtained a copy of that file and discovered it is a tracking database created by a file backup app called ViceVersa Pro. The database contained a log of files ViceVersa Pro had transferred to a disk named “mybookworld.” While the database did not hold copies of the files themselves, it did record their names and the locations to which they were saved on the MyBook World drive.
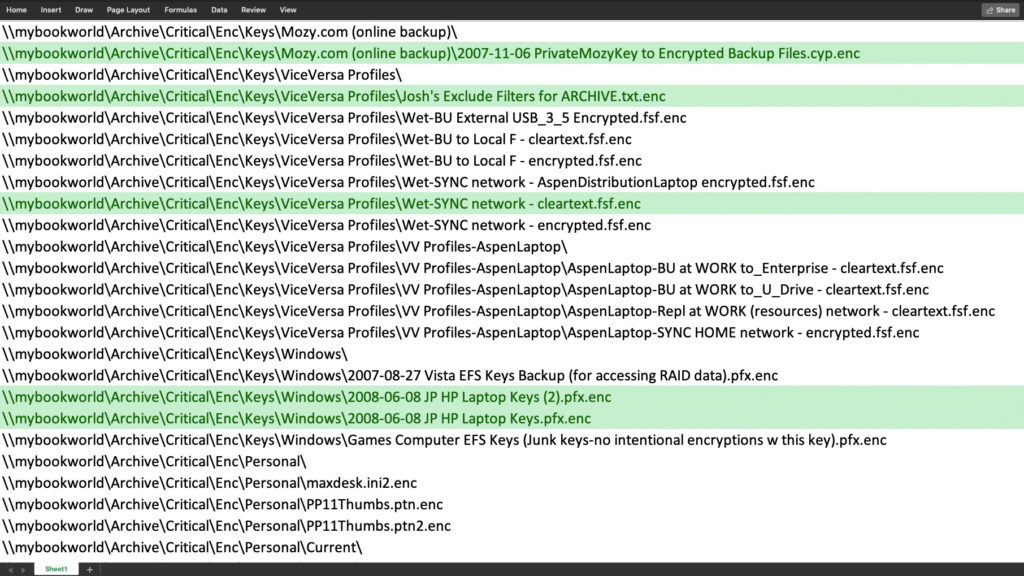
Based on this evidence, Cold believes the ViceVersa Pro database is likely an at least partial log of the files saved to the encrypted Josh Powell hard drive.
Forgotten Password
Josh made an effort to determine whether or not police had gained access to the MyBook World drive in the months immediately following Susan’s disappearance.
His defense attorney, Scott Williams, contacted police by email in March of 2010, requesting the return of his client’s digital devices. West Valley police Sgt. Robert Bobrowski refused, but offered to have detectives seek out any individual files Josh might need.
“If it is in the encrypted section then your client will need to provide the password to help the process move along,” Bobrowski wrote to Williams.
Josh had previously told police he could not remember the password to the encrypted MyBook World drive.
“If possible, pleas send all photos, audio, and video files you can find. There will be some hundreds of gigabytes in total.”
Josh Powell
On April 5, 2010, Josh provided police with a list of files he wanted them to retrieve for him. At the top of the list were his photos and videos, which he described as “basically unreplaceable [sic].”
“Everything that can be released from the white Western Digital drive would be greatly appreciated,” Josh wrote.
West Valley police were unable to accommodate Josh’s request.
In truth, Josh already had copies of many of those files safely in Washington. This became clear after police served a search warrant at the home of Josh’s father, Steve Powell, in South Hill, Washington on Aug. 25, 2011. At that time, they once again seized Josh’s computers and digital devices.

An RCFL examination of those devices revealed some of them contained copies of Josh’s photo and video library, the very files he had claimed were not replaceable.
Decipher Forensics Attacks the Josh Powell Hard Drive
On Feb. 5, 2012, Josh Powell killed himself and his sons, Charlie and Braden. The murder-suicide forever deprived police of the possibility that Josh might voluntarily provide the password for the MyBook World drive. The subsequent release of West Valley’s redacted case files in May 2013 publicly revealed for the first time the existence of the still-encrypted Josh Powell hard drive.
Richard Hickman, who was then a partner in a Utah-based digital forensics firm called Decipher Forensics, saw media reports about the encrypted drive. He contacted Susan’s father, Chuck Cox, and offered to attempt to crack the encryption.
“I reached out and said ‘hey, we’d be willing to take a look at it at no charge,’” Hickman said.

Another partner at Decipher, Mike Johnson, had built a pair of powerful computers to mine cryptocurrency. Hickman told Cox those machines could also be used for password cracking. Cox convinced West Valley police to meet with Decipher.
Police case records showed Detective Ellis Maxwell, the now-retired lead investigator on the Powell case, provided Decipher with a copy of the MyBook World drive in December of 2013.
Box Within A Box
Trent Leavitt, a third partner at Decipher, said they put their computers to work on what’s known as a dictionary attack in an effort to guess the password. The dictionary was built off of lists of common passwords collected from past data breaches. Special software used that dictionary, along with variations, to attempt to unlock the encryption.
After a period of time, the software reported success. It had discovered that the encryption on the MyBook World drive accepted the password “ap1124.”
“It’s six characters,” Trent said. “It’s really simple.”

However, when Decipher attempted to access the drive, they discovered it was blank. This led them to believe that Josh had utilized a feature of True Crypt that allowed for the creation of invisible encrypted partitions nested within encrypted volumes. In essence, a box within a box.
“There might not even be a second layer,” Hickman said. “It could just be, we cracked that top code and it was an empty hard drive.”
Burnout
The Decipher Forensics team put their machines back to work in an effort to crack the suspected second layer of encryption. The software ran through billions of possible passwords.
“That thing would run around the clock, 24/7, for months, if not, you know, close to two years before those things burned up,” Trent said. “And still didn’t break it.”
In October of 2017, word leaked that the Decipher team had succeeded in cracking a password for Josh’s MyBook World hard drive. However, West Valley police had Decipher under a non-disclosure agreement. They were legally prohibited from discussing their work.
“We didn’t talk about the fact that we were even doing it with anybody.”
Richard Hickman
A short time later, the firm Eide Bailly purchased Decipher Forensics. Richard Hickman and Mike Johnson left the company, but Trent Leavitt brought their copy of the MyBook World drive to Eide Bailly’s new state-of-the-art digital forensics lab in Lehi, Utah.
His work on the Powell case has continued there, when time and resources have permitted.
“Most of its done after hours,” Trent said. “We’ll get together as a group and meet and pull our computers out and start working on it. We’ll collaborate on whiteboards.”
Focusing Sunlight on the Josh Powell Hard Drive
The public revelation of Decipher’s work in late 2017 drew the attention of cybersecurity analyst Rob Burton. He worked for a large corporate employer in West Valley City as a digital forensics specialist and had a keen interest in the Susan Powell case.
“The Susan Powell case had a big impact on me personally,” Rob said. “I was aware of it 10 years ago when the news first broke of Susan’s disappearance and the involvement of Josh Powell.”
Rob decided to approach West Valley police. Like the team from Decipher Forensics and Eide Bailly, he offered to volunteer his time and expertise to the password cracking effort. Police accepted his offer and provided him with a copy of the MyBook World drive. They also required that he sign a non-disclosure agreement.

“I knew I just couldn’t just create a folder on my computer called ‘Susan Powell project’ because I was under NDA and kind of had to keep it hidden,” Rob said.
He decided to give that folder the codename “Project Sunlight.”
“There’s a lot of dark things related to this case. And especially after listening to the Cold podcast. Josh, Steven and some of their activities and efforts and a lot of dark subject material. But there’s hope and there’s light,” Rob said. “Sunlight is the best disinfectant, I think.”
Episode credits
Research, writing, hosting and production: Dave Cawley
Production assistance: Danielle Prager, Adam Mason
Additional voices: Kristen Sorensen (as Susan Powell), Eric Openshaw (as Josh Powell), Ken Fall (as Steve Powell)
Cold main score composition: Michael Bahnmiller
Cold main score mixing: Dan Blanck
Supplemental music: Dave Cawley
KSL executive producers: Sheryl Worsley, Keira Farrimond
Episode transcript: https://thecoldpodcast.com/season-1-transcript/project-sunlight-josh-powell-encrypted-hard-drive-full-transcript
KSL companion story: https://www.ksl.com/article/46688866/cold-pornographic-images-at-center-of-custody-case-werent-josh-powells







